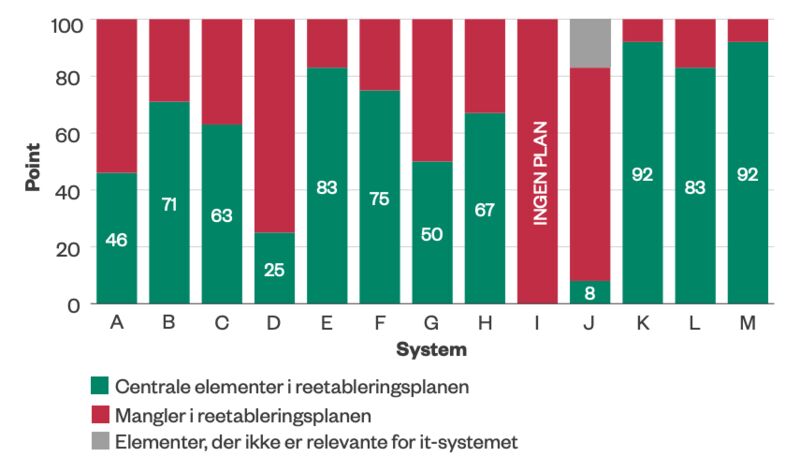
Cloud services mean you are at the mercy of someone else. It is bad enough that hackers broke into Western Digital’s My Cloud service and encrypted their customer’s data. But many private customers are now learning what it means to use WD’s cloud-based login service. It means that even though your data is stored on your own NAS device in your own basement, you still cannot get at it when WD is down.
If you are using any cloud-based login service in your organization, ask your CISO how people would log in and access ressources if that service is down.